
The field of risk management, including risk assessment and mitigation, has seen significant growth in the past 30 years, highlighting the increasing importance of managing risks effectively across various contexts. Drawing on the material that contributes to the new version of CIBSE AM4.1 Security engineering: Strategy, this article will introduce security risk management processes for building services engineering applications.
Security risk management goes hand-in-hand with business continuity and resilience, and each benefits from the active input of dedicated professionals. Designers of built environments must understand appropriate security concepts so that they can identify requirements and technologies in order to integrate them into their designs for a specific project.
Built environments can have a variety of potential security risks that may be influenced by actions, designs, operations, and processes that are associated with the activity of the building services engineer.
These may include a diverse range of areas such as: perimeter and internal security; access control; theft prevention; vandalism control; terrorism and natural disaster; threats to the person; fire safety; environmental and biological safety; occupant health and safety; information, document, IT and cyber security.
Once threats, mitigation options and a strategy are defined, security engineering comes into play. This focuses on designing, specifying and integrating physical, technical, and procedural security measures. Prior to attempting to develop designs for security measures, it is essential to properly define what needs protection by identifying valuable assets in the built environment, and how these may be threatened.
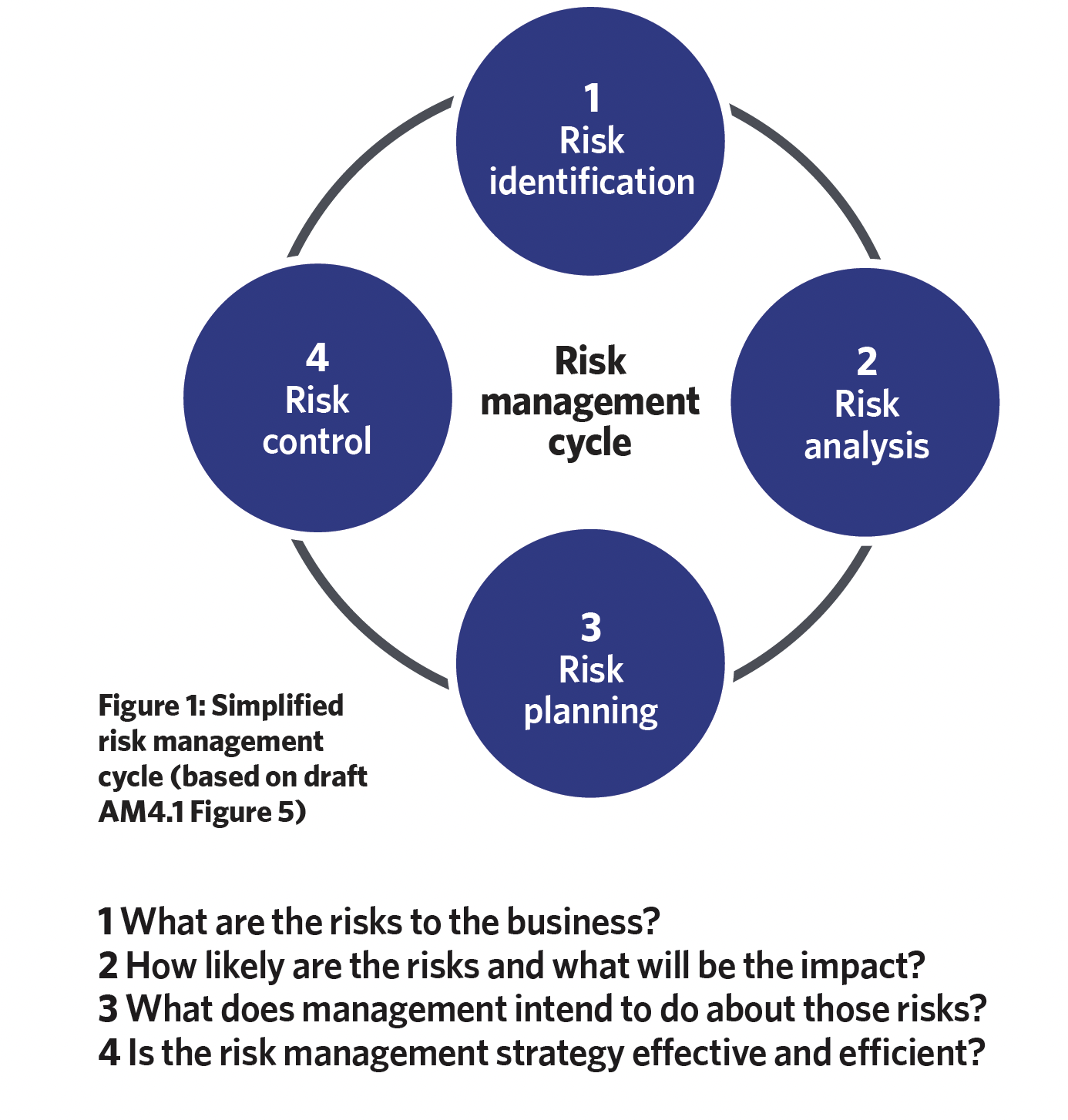
A holistic – and likely cyclic – approach will identify threats, which will help to achieve desired security outcomes, ultimately reducing vulnerability and risk, as illustrated in the simplified example risk management cycle of Figure 1.
Security engineering contributes just one aspect of the procedure and resides towards the end of the security risk management process, relying on prior risk assessments, prioritisation and decision-making.
Building services engineers, while experts in making buildings function, typically lack the specialised skills required to design and specify technical security systems within a defined security strategy, and so collaboration with security professionals provides a valuable, if not essential, pathway to a holistic risk assessment, management and mitigation process.
Security in the built environment should be a structured and transparent process, with solutions tailored to the specific risks and needs of each project, and it is unlikely to be satisfied with generalised solutions. It must be planned and designed collaboratively with other disciplines such as architecture, civil and structural engineering, and landscape architecture.
While traditional threat assessments focus on motive and capacity (intent and capability), a comprehensive understanding demands broader examination. Group dynamics, past activities, ideological motivations, preferred attack methods, and the wider security landscape all play crucial roles. Different threats and tactics necessitate a tiered system for categorising their severity, ensuring clarity and precision. Table 1 provides an example of this gradation.

Vulnerability assessments quantify the likelihood of assets succumbing to an attack. They evaluate the effectiveness of potential measures (deter, detect, delay/deny, respond, recover (DDDRR)) and ensure no weak links compromise the entire system. Similarly to the graded threat levels, a vulnerability rating system can be established defining categories from very low to very high vulnerability.
The effective risk assessment process goes beyond just the ‘who’ and ‘how’ of potential threats; it delves into the likelihood of a threat materialising and the resulting consequences. By understanding these two factors, risks may be effectively prioritised and appropriate resources allocated.
Traditionally, some consider ‘likelihood’ solely as a function of threat and vulnerability levels. While this may work in certain scenarios, it may overlook crucial factors such as asset criticality and target attractiveness. A highly desirable target under high threat with significant vulnerabilities will naturally have a higher chance of attack.
‘Consequence’ is the overall impact of a security event, encompassing areas such as human harm, financial loss, reputational damage and business continuity disruption. While these are common areas of analysis, other specific impacts may be relevant, depending on the project. The combination of likelihood and consequence determines the overall rating of a risk event, which is often visualised through a risk assessment matrix, such as the example in Figure 2, providing a clear basis for stakeholders to evaluate and prioritise risks.
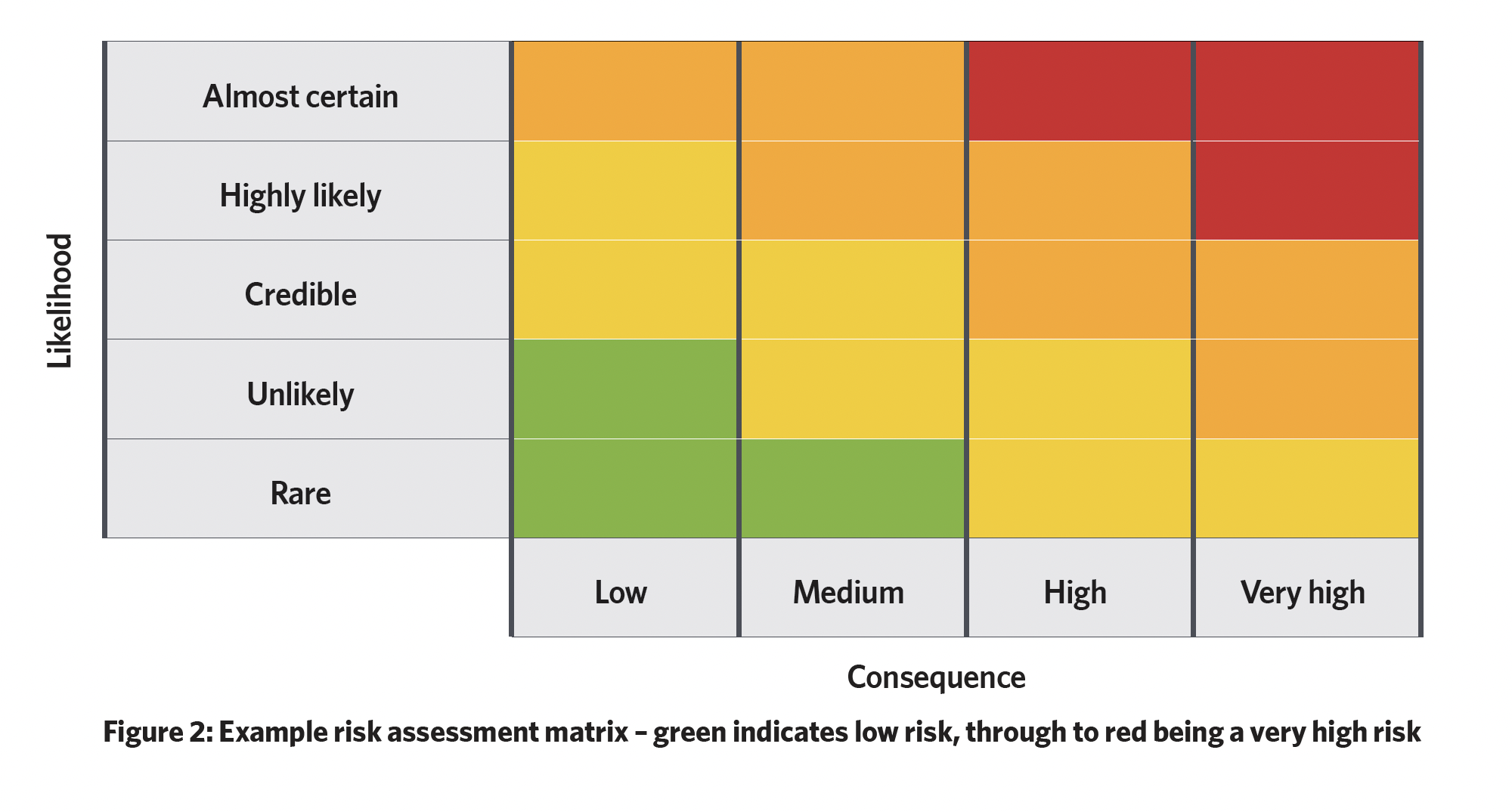
While attempts exist to quantify risk through numerical values, these should be approached with caution. Security risk assessments are inherently qualitative, and assigning arbitrary numbers can be misleading. Once assessed, risks must be prioritised for management or mitigation.
This crucial step aims to identify which risks require active intervention and which can be accepted or tolerated. For example, ‘very high’ and ‘high’ risks may be prioritised for management to reduce both likelihood and consequence. Conversely, low-impact, low-likelihood risks can be accepted with minimal monitoring.
However, other scenarios require more nuanced decision-making, such as risks with low likelihood but catastrophic consequences, or high likelihood but lower consequences. Ultimately, ‘very high’ and ‘high’ risks should inform the development of ‘most-credible, worst-case scenarios’ (MCWCS), which guide risk management actions.
The prioritisation of risks and MCWCS should be formally documented in a project security brief to ensure awareness across stakeholders. Typical key outputs that built environment security risk management professionals deliver as part of the development of a security brief are shown in Table 2.

The risk assessment process would typically require the input provided by security consultants and security engineers. Security risk consultants focus on the big picture – assessing risks, developing comprehensive security strategies, and integrating physical, technical, and operational measures. They are the architects of the overall security approach, playing a leading role early on in planning and design, establishing the foundation and overall security strategy while ensuring harmony with other project goals. They may also offer input on new technologies.
During construction, the consultant takes a light, oversight role to ensure the designed security strategy stays on track; post-construction, they become more involved, participating in security reviews, audits, and oversight activities to guarantee ongoing risk management.
Security engineers focus on the specifics – designing, implementing, and maintaining the technical and physical security solutions defined in the strategy. They are the builders and implementers of the security plan, and are primarily involved later in the detailed design and technical stages. They focus on designing, installing, and commissioning security equipment.
In essence, consultants analyse and plan throughout the project life-cycle, while engineers execute the technical details through the design and build. Both are crucial for effective security, but their skills and contributions differ throughout the risk management process.
To meet the demands of each individual project, the risk management process sets out a series of steps for tackling potential issues. It starts with pinpointing risks, followed by in-depth analysis, prioritisation, solution implementation and ongoing monitoring. These steps, often laden with paperwork and administrative tasks, have paved the way for software-assisted frameworks.
Many frameworks and standards have been developed to guide risk management practices, most notably BS ISO 31000:2018,1 which provide standardised approaches and best practices for identifying, analysing, and controlling risks. The presence of multiple frameworks might be reflective of the complex and nuanced nature of risk management, each offering tailored approaches depending on the specific context and needs.
There are several common routes to integrate security into a project. The most suitable route will depend on the specific security needs of the project.
A security-needs assessment (SNA) may be employed to identify site-specific security risks and vulnerabilities that would involve consultation with stakeholders, including the police. A successful SNA (including implementing recommendations) may be used to achieve Breeam ‘HEA 06 – Security’ exemplary level credit.2 The Breeam guidance2 provides a useful definition for what is considered as a ‘Suitably Qualified Security Specialist’ (SQSS) for the purposes of such work.
Secured by design (SBD)3 focuses on incorporating security measures into properties by accrediting security products and developments. This is operated by the UK Police Services as their preferred scheme for demonstrating how security has been integrated into a new development to deter criminal and anti-social behaviour through the design, layout and specification of buildings and the spaces around and between them. It may be used to meet specific area planning conditions.
SABRE4 is jointly operated by The Security Institute and BRE and is aimed at reflecting best practice in security risk management by emphasising security that is appropriate, proportionate and fit for purpose. It establishes the required documentation to evidence security decision-making. SABRE certification is a reflection of the security risk management process and documentation of security decision-making on a project and, in itself, does not specifically indicate that a development is more secure. Breeam guidance2 defines what constitutes a SABRE professional.
A full security design methodology is a comprehensive approach to security design involving a detailed risk assessment and design process that is recommended for complex projects where security is critical. This integrates qualified security consultants throughout the entire project life-cycle (planning, design, construction, handover), and tasks are often mapped to the RIBA Stages.
Standard design applies pre-determined security measures based on industry standards, but may not be suitably tailored to specific project risks. This is often adopted for simpler projects where security isn’t a primary concern. Typically employed by building services engineers, lacking secure risk assessment. This may risk incomplete security solutions and misaligned measures, as well as potentially unnecessary costs.
A defined planning process may be set by local authorities with specific security requirements and will vary by jurisdiction.
Reducing all risks to zero is often impractical. Therefore, risk management aims to reduce risks within the risk owner’s acceptable range, typically to ‘as low as reasonably practicable’ (ALARP). While security regimes cannot directly influence threat levels, they can significantly impact vulnerability and potential consequences. This is where the focus of risk management lies – reducing vulnerabilities through physical, technical, and operational measures (including user management). This relies on continuous communication, coordination, monitoring, and review. This iterative approach ensures risk mitigation measures are effective and residual risks are understood.
Until such time as these leading practices become more widely adopted throughout the development industry, it is likely that building services engineers may still be requested to undertake security engineering activities. This practice, and the reliance on procured physical and technical security solutions in the absence of a risk-based strategy, should be discouraged.
If a building services engineer — or even a security engineer — is procured only to provide security systems design at RIBA Stages 3 or 4, it is likely that there will be significant gaps in the overall strategy, as the solutions will not be based on a sound foundation for technical systems design and will not be integrated with the physical and operational security measures. As a result, it will not be possible to confidently state that the project’s security is holistic, balanced, proportionate to the risks, appropriate to the context, and effective at reducing vulnerability and consequences.
On its own, a building services engineering approach may not be able to demonstrate that security is fit for purpose, as there is nothing against which to benchmark design or measure the efficacy of the security solution.
This results in simply having security that may be good, but which is unable to be judged positively or defended in any meaningful way, or contribute to the ‘golden thread’ of assurance through the project by tracking risk, mitigation, and residual risk monitoring.
Further reading
CIBSE AM 4.1 Security engineering: Strategy
References:
- BS ISO 31000:2018: Risk management. Guidelines, British Standards Institution 2018.
- bit.ly/CJFeb24CPD1 – accessed 1 January 2024.
- Secured By Design: bit.ly/CJFeb24CPD2 – accessed 1 January 2024.
- bit.ly/CJFeb24CPD3 – accessed 1 January 2024.

